Defence Evasion Technique: Timestomping Detection – NTFS Forensics
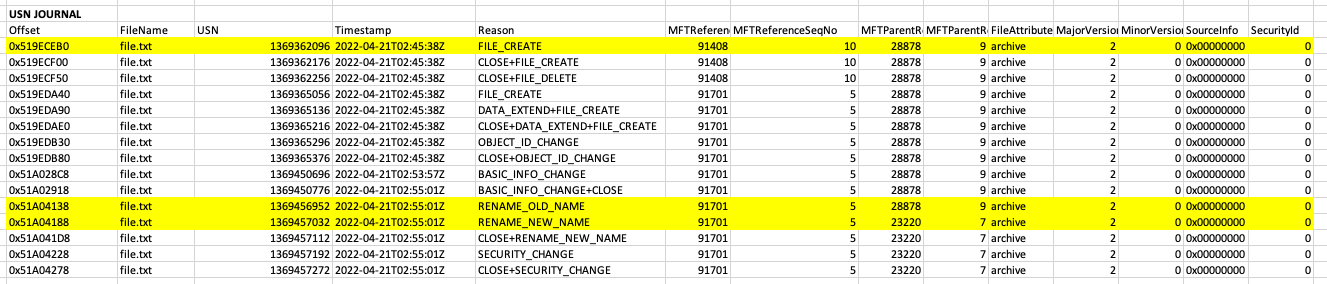
Forensic analysts are often taught two methods for detecting file timestomping that can lead to blind spots in an investigation. The two most well-taught methods for analysts to detect timestomping are: Compare the $STANDARD_INFORMATION timestamps vs the $FILE_NAME timestamps in the Master File Table (MFT) Look for nanoseconds in a timestamp matching “0000000” as this often shows the use of an automated tool (i.e. Metasploit) These two detection methods are based on two fallacies that I will explore in this blog post: Myth 1: $FILE_NAME timestamps cannot be timestomped Myth 2: Attacker tools cannot alter nanoseconds in a timestamp INTRODUCTION TO TIMESTOMPING Timestomping is a technique where the timestamps of a file are modified for defence evasion. Threat actors often perform this technique to blend malicious files with legitimate files so that when an analyst is performing IR, critical evidence escapes detection. Timestomping using tools like Cobalt Strike (of...
